Wireshark pcap 파일 분할
이번 핵더 패킷에서 재일 고생했던 부분은..
시간과의 싸움이였다..
제공된 pcap 파일의 크기는 약 250M 정도..
하지만 이 파일을 읽어서 필터걸고 TCP follow 등 분석하는데 로딩 시간이 상당히 걸렸다..
대회시간은 단 2시간…
따라서 빠른분석을 위해 패킷을 의미있는 단위로 쪼개서 분석했어야 했는데 하는 아쉬움이 많이 남았다.
1. editcap을 이용한 분할
Wireshark를 설치한 폴더에 보면 editcap.exe 가 있다.
말그대로 pcap 파일을 편집 및 변환을 하는 도구다..
C:\Program Files\Wireshark>editcap.exe
Editcap 1.10.1 (SVN Rev 50926 from /trunk-1.10)
Edit and/or translate the format of capture files.
See http://www.wireshark.org for more information.
Usage: editcap [options] ... <infile> <outfile> [ <packet#>[-<packet#>] ... ]
<infile> and <outfile> must both be present.
A single packet or a range of packets can be selected.
Packet selection:
-r keep the selected packets; default is to delete them.
-A <start time> only output packets whose timestamp is after (or equal
to) the given time (format as YYYY-MM-DD hh:mm:ss).
-B <stop time> only output packets whose timestamp is before the
given time (format as YYYY-MM-DD hh:mm:ss).
Duplicate packet removal:
-d remove packet if duplicate (window == 5).
-D <dup window> remove packet if duplicate; configurable <dup window>
Valid <dup window> values are 0 to 1000000.
NOTE: A <dup window> of 0 with -v (verbose option) is
useful to print MD5 hashes.
-w <dup time window> remove packet if duplicate packet is found EQUAL TO OR
LESS THAN <dup time window> prior to current packet.
A <dup time window> is specified in relative seconds
(e.g. 0.000001).
NOTE: The use of the 'Duplicate packet removal' options with
other editcap options except -v may not always work as expected.
Specifically the -r, -t or -S options will very likely NOT have the
desired effect if combined with the -d, -D or -w.
Packet manipulation:
-s <snaplen> truncate each packet to max. <snaplen> bytes of data.
-C <choplen> chop each packet by <choplen> bytes. Positive values
chop at the packet beginning, negative values at the
packet end.
-t <time adjustment> adjust the timestamp of each packet;
<time adjustment> is in relative seconds (e.g. -0.5).
-S <strict adjustment> adjust timestamp of packets if necessary to insure
strict chronological increasing order. The <strict
adjustment> is specified in relative seconds with
values of 0 or 0.000001 being the most reasonable.
A negative adjustment value will modify timestamps so
that each packet's delta time is the absolute value
of the adjustment specified. A value of -0 will set
all packets to the timestamp of the first packet.
-E <error probability> set the probability (between 0.0 and 1.0 incl.)
that a particular packet byte will be randomly changed.
Output File(s):
-c <packets per file> split the packet output to different files
based on uniform packet counts
with a maximum of <packets per file> each.
-i <seconds per file> split the packet output to different files
based on uniform time intervals
with a maximum of <seconds per file> each.
-F <capture type> set the output file type; default is pcapng.
an empty "-F" option will list the file types.
-T <encap type> set the output file encapsulation type;
default is the same as the input file.
an empty "-T" option will list the encapsulation types.
Miscellaneous:
-h display this help and exit.
-v verbose output.
If -v is used with any of the 'Duplicate Packet
Removal' options (-d, -D or -w) then Packet lengths
and MD5 hashes are printed to standard-out.
C:\Program Files\Wireshark>
이 editcap을 이용해서 pcap 파일을 분할 할수 있다.
1) 30만개 패킷씩 분할
D:\>editcap.exe -c 300000 original.pcap original_split.pcap
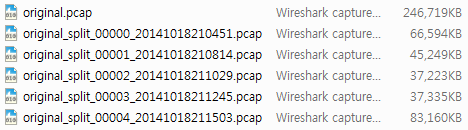
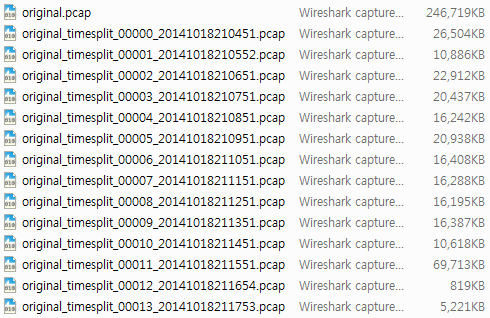
2) 60초 단위로 분할
D:\>editcap -i 60 original.pcap original_timesplit.pcap
3) 특정 시간 부분만 추출
D:\>editcap -A “2014-10-18 21:06:00” -B “2014-10-18 21:07:00” original.pcap original_timerange.cap
![]()
4) 특정 패킷만 선택하여 저장
D:\>editcap -r original.pcap original_selected.pcap 200-300 500-700
![]()
5) 특정 패킷만 제외하고 저장
D:\>editcap original.pcap original_unselected.pcap 200-300 500-700
![]()
만일 패킷을 마우스 오른쪽 버튼으로 쉽게 분할하려면..
Editcap_Split300000.zip 파일을 다운받아 설치하면 된다.
그러면 마우스 오른쪽 버튼에 Editcap_Split300000 메뉴가 생기고, pcap 파일을 Editcap_Split300000 을 이용하여 30만 패킷 단위로 분할할 수 있다.(단, Wireshark 위치가 PATH에 설정되어 있어야 함)
2. SplitCap 세션별로 저장
http://splitcap.sourceforge.net/
SplitCap은 pcap 파일을 분할해주는 도구이다.
D:\SplitCap_2-1>SplitCap.exe
Usage: SplitCap [OPTIONS]...
OPTIONS:
-r <input_file> : Set the pcap file to read from.
Use "-r -" to read from stdin
-o <output_directory> : Manually specify output directory
-d : Delete previous output data
-p <nr_parallel_sessions> : Set the number of parallel sessions to keep in
memory (default = 10000). More sessions might be needed to split pcap
files from busy links such as an Internet backbone link, this will however
require more memory
-b <file_buffer_bytes> : Set the number of bytes to buffer for each
session/output file (default = 10000). Larger buffers will speed up the
process due to fewer disk write operations, but will occupy more memory.
-s <GROUP> : Split traffic and group packets to pcap files based on <GROUP>
Possible values for <GROUP> are:
flow : Flow, i.e. unidirectional traffic for each 5-tuple,
is grouped together
host : Traffic grouped to one file per host. Most packets
will end up in two files.
hostpair : Traffic grouped based on host-pairs communicating
nosplit : Do not split traffic. Only create ONE output pcap.
(default) session : Packets for each session (bi-directional flow) are
grouped
seconds <s> : Split on time, new file after <s> seconds.
packets <c> : Split on packet count, new file after <c> packets.
-ip <IP address to filter on>
-port <port number to filter on>
-y <FILETYPE> : Output file type for extracted data. Possible values
for <FILETYPE> are:
L7 : Only store application layer data
(default) pcap : Store complete pcap frames
-z : Lazy file creation, i.e. only split if needed
-recursive : Search pcap files in sub-directories recursively
Example 1: SplitCap -r dumpfile.pcap
Example 2: SplitCap -r dumpfile.pcap -o session_directory
Example 3: SplitCap -r dumpfile.pcap -s hostpair
Example 4: SplitCap -r dumpfile.pcap -s flow -y L7
Example 5: SplitCap -r dumpfile.pcap -s seconds 3600
Example 6: SplitCap -r dumpfile.pcap -ip 1.2.3.4 -port 80 -port 443 -s nosplit
Example 7: SplitCap -r C:\pcaps\ -recursive -s host -port 53 -o DNS_dir
Example 8: tcpdump -n -s0 -U -i eth0 -w - | mono SplitCap.exe -r -
D:\SplitCap_2-1>
editcap 보다 좋은 기능은 세션별로 분할해준다는 것이다.
D:\SplitCap_2-1>SplitCap.exe -r original.pcap
실행하면 pcap 파일명과 동일한 디렉토리를 만들고 그안에 세션별로 패킷을 쪼개서 저장해준다.
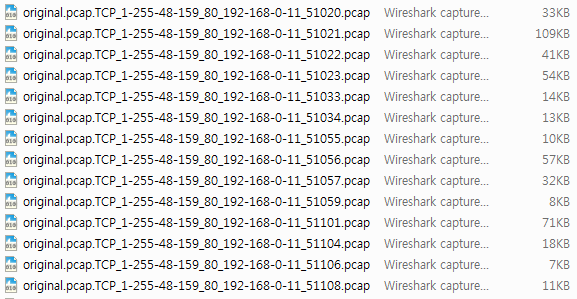
단, 세션이 많은 경우 파일이 많이 생성되므로 주의..
3. Tshark 을 이용해 캡쳐시 분할하기
전XX 책임님꼐서 알려주심 팁~
tshark -D 으로 인터페이스 확인.
tshark -i 7 -w test.pcap -b filesize:10000
filesize 를 10M 단위로 파일 저장
참고 :
http://www.packetinside.com/2010/01/%EB%B6%84%EC%84%9D%ED%95%A0-%ED%8C%A8%ED%82%B7-%EB%8D%B0%EC%9D%B4%ED%84%B0-%ED%81%AC%EA%B8%B0%EA%B0%80-%ED%81%B0-%EA%B2%BD%EC%9A%B0%EB%8A%94-%EC%9D%B4%EB%A0%87%EA%B2%8C-%ED%95%98%EC%9E%90.html
http://www.packetinside.com/2010/07/%EC%9C%88%EB%8F%84%EC%9A%B0%EC%97%90%EC%84%9C-%EB%A7%88%EC%9A%B0%EC%8A%A4%ED%95%9C%EB%B2%88%EC%9C%BC%EB%A1%9C-%ED%8C%A8%ED%82%B7%ED%8C%8C%EC%9D%BCpcap%EC%9D%84-%EB%B9%A0%EB%A5%B4%EA%B3%A0-%EC%89%BD%EA%B2%8C-%EB%B6%84%ED%95%A0%ED%95%98%EC%97%AC-%EB%B3%B4%EC%9E%90.html
http://www.packetinside.com/2010/05/tcp-udp-%EC%84%B8%EC%85%98%EB%B3%84%EB%A1%9C-%ED%8C%A8%ED%82%B7pcap-%ED%8C%8C%EC%9D%BC-%EB%B6%84%ED%95%A0%ED%95%98%EA%B8%B0.html

One Response to Wireshark pcap 파일 분할